Virtual Private Networks are a common remote access technique in the world today. They allow internet service providers to give private tunnels via the public cloud to achieve productivity at the same time economize on costs from remote access services. A VPN is simply an extension of an organization’s intranet through a public network establishing a secure link via a private tunnel. A Network Address Translation on the other hand is a networking device that is essentially helpful in providing shared internet access. NAT is also helpful in isolating VPN networks. They simply lockout data directly transmitted between various private network nodes. Since NAT cannot operate effectively with encryption protocols, therefore, VPN and NAT combine to enforce a complexity layer to VPN deployments augmenting their security. This report examines VPN and NAT with the intention of highlighting its architectures, advantages, and disadvantages as well as the software used to implement both technologies.
Over the past few years, most organizations have augmented their mobility by allowing its employees to easily communicate. Most employees also demand flexibility such that regardless of their locations they can remain connected to the organizations network. With globalization, organizations network have been spread across the universe. Such a scenario, demands the need for a reliable and secure architecture to interconnect peers, servers, networks across the world. The use of a virtual private network presents an ideal solution to such predicament, VPN and NAT provides a secure solution that makes it hard for intruders to breach organizational information from outside the organizations premises. Network address translation does adds a security feature to virtual private networks and with the current network trends, security has always been a major challenge in implementation of networks.
Purpose of VPN and NAT
A virtual private network is a way of improving an organization’s security as well as network resources. Its purpose is to allow organizations to connect remote workplaces to private networks. Employees working remotely can operate as if they are physically connected to the network. VPN actually allows all services that would be available in a typical Local area network such as print and file sharing, web access as well as instant messaging. Furthermore, it allows an organization’s employees to avoid reconnection to network resources when using VPN such that it supports universal naming convention and drive letters with little or no modification.
The purpose of Network address translation on the other hand is to handle all conversions of the public network IPs to private IPs as well as reveal public IPs only on the global network, hiding the private network IPs. This ensures security on the basis that every outgoing or incoming communication must go via a conversion procedure that also gives an opportunity to authenticate or qualify the communication or match it with similar previous communication. Furthermore, network address translation also serves as a firewall in the routing process hence enabling an extra security layer between the organization and the internet.
Architecture of VPN and NAT
A virtual private network has a number of geographically distinct sites that are all securely connected over a shared public infrastructure. Internet protocol-based virtual private networks allow employees to easily get the same connectivity, security, and reliability from private networks and could assist in providing dial-in access, intranet, extranet, and internet services. Virtual private networks can be configured in four distinct ways. One may have firewalls and routers that are connected together to the logical or physical lease carrier line or service providers. Another may have a set of intrusion detection, proxy firewall, key management, encryption, and tunneling. VPN may also be managed internally or delegated to a service vendor. Irrespective of whether or not there is remote access to the intranet or extranet for the VPN, the chosen service provider should be able to collectively integrate all the services to a comprehensive solution.
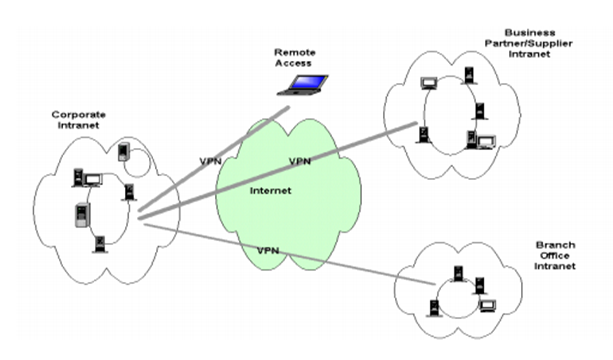
Below is a figure of a simple VPN architecture with end to end services across the internet.
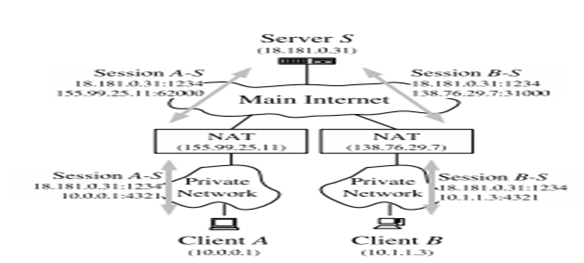
Network address translation architecture
NAT is also implemented in various ways where each architecture affects the underlying protocols differently. The most reliable architecture for VPN communications and network address translations is having communications as a standard client/server communication network, via relaying. As highlighted on the architectural diagram below, two client hosts A and B each initiates a connection to a server S. The clients are within different virtual private networks and each of their network addresses translations prevents each client from initiating connections directly to the other.
The only channel for communication is through the server, or in some cases a router that then routes the communication to the target recipient. Every network address translation architecture has situations in which they are desirable. As a result, other architectures could be more ideal in certain situations than others, some are even sophisticated and costly to implement. However, since there is no architecture that is more ideal and reliable on all network address translations, relying upon the best option if maximum robustness is to be achieved.
Advantages
This technology thus provides flexibility and security through sophisticated authentication and encryption protocols thus protecting data from being compromised. There is also an advantage in that information can be remotely accessed even from locations far from company premises, it, therefore, helps in improving productivity. There is also an aspect of reduced costs in that the technology once implemented has fewer maintenance costs. Furthermore, if this is implemented through a service vendor, surveillance and set up costs are outsourced to the vendor.
Disadvantages
The drawbacks are that there is no quality of service, as well as no guarantee for an end to end throughput with possible packet losses. It is also hard to reserve bandwidth in this technology. With the additional NAT, the technology would be resource consuming on the basis that since there is a need to convert IP addresses for all inbound and outbound traffic as well as store conversion information. With this technology, there is a likelihood that some applications and technologies may not function as expected.
Software used to implement VPN and NAT
SoftEther VPN
This is a global and powerful multi-protocol virtual private network software that is compatible with Linux, windows and mac platforms. This is an open-source product that allows administrators to use for commercial and personal use without paying any fees. It also has a formidable resistance against firewalls. It is founded on a Network address translation traversal and penetrates company firewalls providing more security. This software allows network administrators to implement VPN and NAT in a company allowing employees to access that VPN without altering the firewall settings. This product is compatible with the world’s most popular current networking products such as L2TP, EtherIP, IPsec, and Cisco routers.
OpenVPN
This virtual private network software is flexible and robust. It has support for Ethernet bridging, SSL/TLS security, UDP, or TCP tunnel through NAT or transport proxies. It also supports traditional encryption mechanisms such as the use of pre-shared keys and public security keys. It has been developed to operate with virtual private networks allowing administrators to create secure VPNs that can accommodate many clients. This also makes use of all authentication, encryption, and Open SSL library certificates to safeguard private networks.
Soft Ether VPN vs. Open VPN
The fact that SoftEther is a bit of a new software product to implement this technology, it has taken a different dimension that seeks to provide exclusive high-end security as well as ensuring that network users enjoy platform compatibility. Despite the fact that the two technologies are both open-source, SoftEther was a product of an academic study as opposed to an OpenVPN which was developed by a company. As opposed to OpenVPN which only provides support soft its protocol, SoftEther supports L2TP, SSTP, AND IPsec. Speed is also a factor that brings out a great difference between the two software products, OpenVPN allows up to 100Mbps of speed, SoftEther can be scaled up to a speed of 900 Mbps with an opportunity to be scaled further.
OpenVPN has also been around for so long and is compatible with more platforms as compared to SoftEther. SoftEther supports android, Windows, Linux, iOS, FreeBSD, and Solaris while OpenVPN supports all these platforms plus an extra two platforms namely NetBSD and QNX. SoftEther excels with regard to better flexibility and speed. Nevertheless, Open VPN is reliable, stable, and very secure with no compromise by hackers. The fact that SoftEther is a new technology enables it to provide more features and better functionality.
Virtual private networks and Network address translation allow organizations to connect to remote offices within a public network while equally sustaining the security of communications. The secure links appear to users as if they were private network communications regardless of it being facilitated by a public network. This technology addresses challenges facing current business environments with the shift towards a rise in telecommuting and international operations, in which employees should be able to connect to a centralized Headquarters in order to communicate and access resources needed for them to carry out their duties effectively. VPN and NAT is a rather new technology in networking but totally necessary with respect to the challenges faced in the networking world. Software products implementing this technology are still scarce and limited in functionality, but hopefully, the field will attract more developers and investors in the future.



